So, let's jump into the real show; first thing as usual is booting the VM!
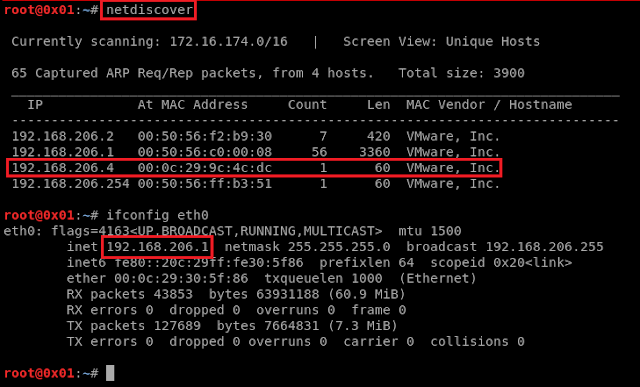
Of course after setting up the virtual machine to NAT Network, so it can talk and chat with the attacking machine (Kali) which is on NAT also! We need to discover the IP address so we can start the game :-DI used nano text editor on the terminal to make the needed changes, I gave it the 'vulnerable' name so we can use that name instead of using the whole IP ^-^
Nmap the well known network scanner, I used it to get the open ports so I can design my plan for attacking the machine (Actually that was a plus, because the machine name mean we are dealing with a web server so need for scanning other ports & services).
Nmap said we have two open TCP ports (22/SSH + 80/HTTP). The command I used simply means a faster scan on all ports (65535 PORTS) on the 'vulnerable' machine with full verbosity so we can understand what nmap doing! I am doing another scan to enumerate the version of those services (Just to get more information about the target).
Okay, enough information from the NMAP let's jump strait away to the web service!
Nice website 👌Let's visit the pages and see if we can get something. We can try doing directory bruteforcing but it is useless, we know it is related to an SQL Injection vulnerability so let's find this vuln!
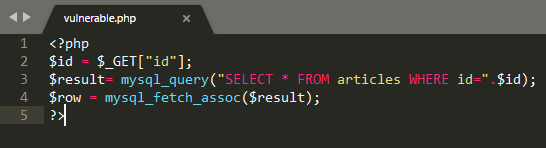
Bingo, by adding (') to the parameter 'id' on the script 'cat.php' we get an SQL Syntax Error. Technically the stupid PHP Code behind this; is the following:
The value provided to the user ($_GET["id]) is directly echoed in the SQL request on the line 3. If a user try to access the URL (/cat.php?id=2'), the following request will be executed (SELECT * FROM articles WHERE id=2').
However, the syntax of this SQL request is incorrect because of the single quote (') and the database will throw an error which is bad (Don't show your stupid debugging & error codes to a HACKER).
The value provided in the URL is directly echoed in the request and considered as an integer, this allows you to manipulate the database and perform bad operations.
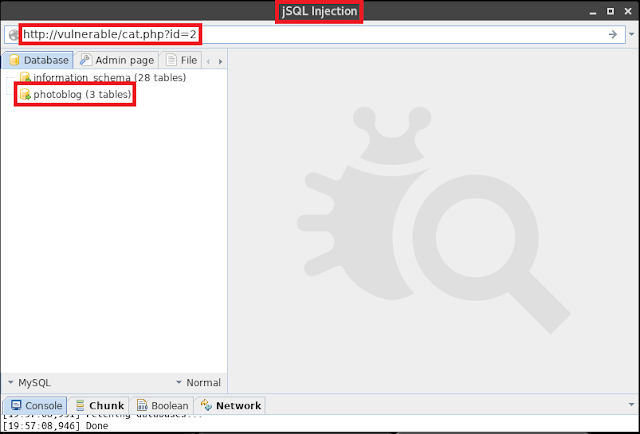
The goal of this article is to provide the walkthrough and not to teach about SQL statements and queries or about SQL Injection Exploitation, so I'm not going to use the professional & long way; instead I'll be using an automated tool to perform the SQL Injection.jSQL is one of the most used SQL Injection Exploitation Toolkits, it helps you save time and do easy exploitation! By giving the vulnerable url to the tool it gives us the whole database, let's find out what is inside the 'photoblog'.
By dumping the target DB, we've got the credentials of the 'admin' user, which is bad :-) The password seem to be hashed in a classic MD5 way :-D Let's break it ;-)
By using a simple toolkit in Kali under the name 'findmyhash' we managed to crack the MD5 Hash and get the real passsword which is 'P4ssw0rd' Let's log in as an 'admin' :-D
Now we are in the administration page :-) Like we see, we can add a new picture so we can upload stuff to the server, generally there is a vulnerability under the name of 'Arbitrary File Upload' basically it allows an attacker to upload a backdoor or shell to the web server! Let's try it ^_^
I've done a little test, to see if it really works, I just created a little pic under the name 'test.jpg' to test the upload feature :-) Let's see the result!
The developer is really a stupid person, he like echoing everything -_-' What a dumb man! Like we see, the pic is successfully uploaded to the target box, let's try to visit it!
After browsing all pics we notice the path of the files! So, it is some kind of path disclosure because if we upload our shell we need to execute it so we need to find the path first and it seem to be clear that everything is under the 'uploads' folder!
Stupid developer with a stupid system administrator can cause this little-big error :-D What is the error Tahar? Really! It is clear DIRECTORY INDEXING, it allows us to see all files because there is no Index file to hide those shits! Let me upload my shell and hack that shit I am bored!!
Yay, One line SHELL :-) Yes I am the most elite hacker in the world 😎 Tahar STFU!
This little one line PHP Shell gives an advantage of executing system commands through the PHP function 'system' in the GET parameter 'cmd'.
It seem like the developer is getting smarter. Oh Yeah, I heard he started learning Web Application Security, so he created this stupid filter to disallow the upload of PHP files! Guys please tell him that he is dealing with ELITE HACKER 😎 Let's bypass it :-D

Unfortunately, I am smarter than the developer :-'( I managed to upload the shell easily by changing the file extension to a capital one 'PhP', JOB is DONE :-D
My little shell is ready for the EXECUTE :-) Let's go and remember the 'cmd' parameter!!
COMPLETELY DONE!!The goal was to get Shell and not to root the machine, because the user is (www-data), there is a chance to root the machine and it is easy; try your luck ;-)
So, I am done writing this long walkthrough -.-' I just hope you liked it and enjoyed this long read! Make sure to share it with your friends and see you InshAllah in the next article ;-) cya!






















perfect man! :)
ReplyDeleteThanks mate!
DeleteNice Writeup!
ReplyDeleteThanks, enjoy and don't forget to share it!
DeleteNice 1 Tahar
ReplyDelete