Let's talk first about the box it self and some information about it for people who still didn't even open/try it:
- Name: Pinky's Palace.
- Version: v1.0.
- Date: 6 Mar 2018.
- Difficulty: Intermediate/Medium.
- Author: Pink_Panther.
- Publisher: Vulnhub.
- More: Pinky's Box on Vulnhub.
- WriteUP: MrTaharAmine.
- NOTE: This BOX works only on VirtualBox.
So, as usual we start the game like a Pen-Test; normal steps (methodology) as usual. After getting my Target VM IP I discover the open ports using Nmap:
 |
| Full PORTS Nmap scan with services version enumeration using a faster scan! |
After, the nmap results we get to know that there is three different stuff:
- 8080: NGinx HTTP Server.
- 313337: SQUID HTTP Proxy (Transparent Proxy).
- 64666: Open SSH Server.
 |
| Accessing the nginx http server port gives HTTP 403 Error Code |
It means we can't access that shit, but I've noticed there is a SQUID Proxy; so let's try to use it for our purpose to bypass that restriction!
Use same settings I used of course by changing the IP to your Target's IP I hope you all know that :-) If not, please stop now and close your browser tab; you are absolutely a NOOB++ :-P (I enjoy trolling sometimes) ^.^ I am sorry if I hurt you; get out of my blog now -.-'
Now, we are able to see the real page through that Proxy :-D Let's continue..
Nothing really in the source code :-[ It is time to use some 'Directory Bruteforcing' we may find some hidden folders/files :-D But, don't forget you need to redirect all your normal requests through the proxy to be able to see if there is a dir/file or not! Without doing that, you are simply just bullshitting around :-P Bunch of toolkits out there (Code yours if you want to waste your time :-D) Choose your favorite and start the brute attack using the medium list (/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt).
I am using OWASP Dirbuster :-D And, after a couple of seconds I've got the directory that I'm looking for ^.^
Let's open it and see what it have!
When I get to see that kind of stuff I go directly and open my lovely hacking toolkit 'Burp Suite' one of the best webapp hacking toolkit's out there!
The real hacking comes here, if you are a little bit familiar with Web Application PenTesting you'll understand exactly what is going. In quick <p> This challenge is simply an SQL Injection Vulnerability (Time-Based) </p> SQLMap can be used through a proxy easily let me try it and see what will happen exactly :-D Sending the request to sqlmap and adding a couple of parameters and boom!
(sqlmap -r /home/pentester/Desktop/vuln.txt --proxy=http://192.168.1.9:31337 --technique=T --level=5 --risk=3 --suffix="" --prefix="" --skip-waf --threads 10 --dbms=MYSQL) ( Go check the sqlmap docs to understand this command ;-) )
It takes a good time (If you are 1337 enough do it manually, the code was not super easy but still possible ;-)
SQLMap results are READY!!
After the successful SQL Injection Attack, I started dumping the DB tables & rows and get to know two users (pinky & pinkymanage)! The password was MD5 Hash so easier to crack but worked for only one account :-[ . After cracking it I get a credential (pinkymanage/3pinkysaf33pinkysaf3). That is the interesting one.
Of course I tried to log in using it 3 times and it won't work :-{ I remembered there was an SSH port during the scan (We need to take notes during a PenTest); So, I jumped to the ssh directly to try it out :-D
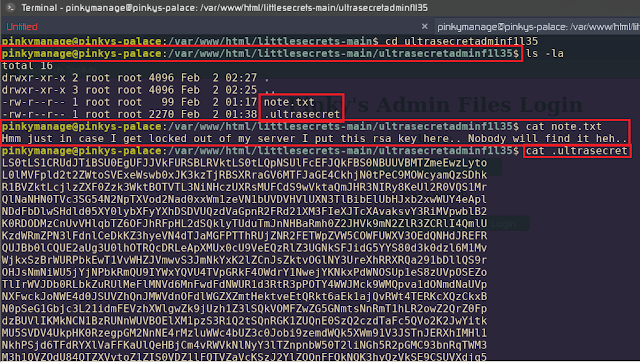
SSH Worked Successfully! Time to go ROOT :-D After a lot of (cd && ls -la) I have got this:
That was nice, the notes say it is an RSA Key so it is probably a Private Key let me try to get the key first; easy it was an easy symmetric cryptography algorithm!
This will teach SysAdmins to never save RSA Private Keys on the same server ;-)
Time to SSH into the new fun! Pinky seem to be the right user to SSH into :-D
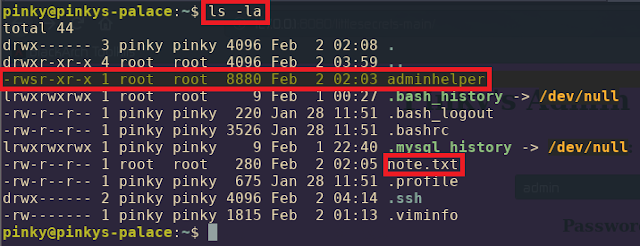
Successful :-D It is time to go root and not to keep switching from user to user -.-'
Reading the notes text file you'll understand that this binary is a C software he made for developing his printing skills (I was like WTF xD) Yeah, that's it! So, easy like it looks a buffer overflow to escalate into the ROOT. If you see the file permissions it is owned/created by the ROOT and executable by ALL. Yummmi <3 Time to do some Reverse Engineering and 0.1% Exploit Development to own a ROOT Account (Finally time to finish that machine).
(Adult Warning: Assembly is for only +18 years old, please close the tab if you are -18) I gave you this warning so I can make sure that you are not going to die after watching some weird codes (assembly) ^.^
Basically, by running the little software. I give Input it takes the input process it and give an Output. It is just printing an Input, that's all!
The segmentation fault is clear and as a 'PenTester' it simply means a Buffer Overflow :-D
After reverse engineering the binary, I get to know the vulnerable call which is (strcpy) through GDB. (The strcpy built-in function does not check buffer lengths and may very well overwrite memory zone contiguous to the intended destination).
The binary challenge was more easier because there is no binary defenses (NX, ASLR..) But there is PIE. So we can’t use the ROP tricks, but we can use Shellcode Injection. Let's do it and finish it OFF!
I've overflown the buffer, overwriting it with the correct address where my Shellcode was stored in the kernel environment and boom DONE; ROOT <3
I don't want to share the flag (Do it by yourself and get the flag ;-))
A big thanks to the following friends & people:
- Brahim Fouad: A big thanks for you bro for helping me to fix my dumb mistake <3
- Pink Panther: A big thanks for your time making the machine <3
- VulnHub: A big thanks to the team for publishing this great box <3


















Nice write up... really helpfull!
ReplyDeleteThank you mate! Make sure to share the link =)
DeleteHonestly, that's weird! I'll look into it again soon. It is time to write the Hard edition Walkthrough ;-)
ReplyDeleteSame for me too, nothing in the response about sleep. Thanks for the write up though i too got stuck at the same place too :)
ReplyDeleteI got the sleep to work directly from burp suite knowing exactly where to put it after the User-agent. However, sqlmap found nothing for me after about 15-20 different attemps. If I was doing this on my own without knowing where the vulnerability was there is no way I would of been able to do what you did.
ReplyDeleteHello I just wanted to know what wordlist you used for directories enums on dirbuster ...
ReplyDelete