Hey CTFers, Boot2root Fans! Today, I'll be doing "Game of Thrones CTF" from VulnHub.
This CTF Box is a challenge-game to measure your hacking skills. Set in Game of Thrones fantasy world. Your goal is booting the machine and getting the root with 11 flags.
Goal:
Get the 7 kingdom flags and the 4 extra content flags (3 secret flags + final battle flag). There are 11 in total.Rules/guidelines to play:
- Start your conquer of the seven kingdoms.
- You'll need hacking skills, no Game of Thrones knowledge is required. But if you play, it may contains spoilers of the TV series.
- Difficulty of the CTF: Medium-High.
- Don't forget to take your map (try to find it). It will guide you about the natural flag order to follow over the kingdoms.
- Listen CAREFULLY to the hints. If you are stuck, read the hints again!
- Powerful fail2ban spells were cast everywhere. Bruteforce is not an option for this CTF (2 minutes ban penalty).
- The flags are 32 chars strings. Keep'em all! you'll need them.
- It's supposed that you don't have physical access to the machine. Don't try to cheat. The challenge is to hack it through the network services.
Requirements/starting guide:
- Import the Linux based CTF challenge virtual machine (OVA file).
- OVA file is compatible with Oracle Virtualbox and Vmware.
- The challenge vm needs 1 cpu and 1512mb RAM to work properly.
- The challenge vm has its network configured by default as bridge. It will take an IP from the DHCP of your network.
Download and more details:
Let's break into the real game * . *
I've just started getting the Box IP, as usual I just use 'NetDiscover' to scan my "NAT" network.
After getting the box IP I decided to give it a hostname that I can remember later on instead of numbers (IP)... I just edited the hosts file!
Of course same as a PenTest, I started scanning for ports to see how the box work..
Full nmap scan of 65535 ports. It is time to enumerate the open services and see what is going on there exactly..
By using the last nmap long command, I've got a very big result.. I will go to analyse it and I will be back 💤😁
Let's start with the normal Web service (HTTP 80) and we get a nice CTF Picture!
I went to see the source code of the HTML Code behind the scene and it was pretty simple!
I didn't see much information so I started running 'dirbuster' on the default webroot to get some files or folders so I can decide where to go next..
Bunch of files and folder, let me go one by one!
But wait, the source code looks weird let me get back and check every file I've found on the index.html!
I started getting frustrated, bunch of hints and words and my brain will start overthinking -.-' They mentioned the word 'music' a lot and true the webpage when it loads it execute a music track; please don't "Steganography" me, I hate this world because I believe it is definitely not realistic and I don't enjoy boot2root boxes that rely on Stegano & Bruteforcing... Not bad, let me continue and see where I can go :-D
Meh, easy! By just using the 'strings' I've got bunch of details and words as usual :-3
First flag like a boss :-P (Secret Flag Number 1).
After running Nikto Web Server Scanner, I've got a bunch of files and folders, most important was robots.txt and sitemap.xml
Let's go now and check the Sitemap & Robots!
This dude wanted to become my friend! He is giving a link to a GoT Map.
The wanted map!
It means there are 7 flags in each service of the box:
I started getting some weird feelings and I went to check again the 'robots.txt':
It was not something just like that, it means I need a specific user agent to let me get it! I started trying to change my user agent and see what happen next..
I edited the user agent to the one specified in the 'robots.txt' file on the webroot directory! I've got another picture and definitely another page:
Now, it is completely another page:
I went back to dirbuster results and I have seen a directory named 'h/i/d/d/e/n':
New hint saying we are on the right direction! Let's continue..
Another big hint appeared inside the source code of that directory index file:
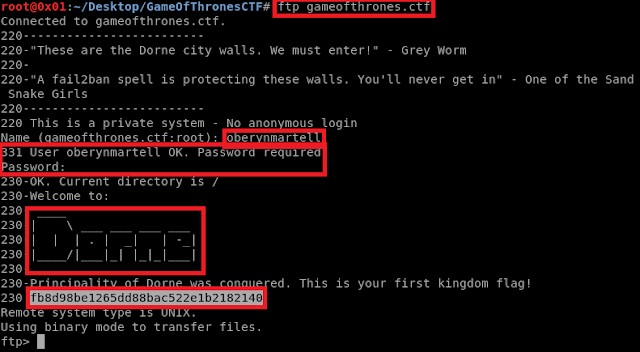
I started linking stuff I have found before and I get to know that to enter the Dorne (FTP) I need to identify my self as 'oberynmartell' and using the password I have found 'A_verySmallManCanCastAVeryLargeShad0w' Let's try it and see what is next :-D

Kingdom's first flag like a boss!
I have got two files, I will examine them and see what can I get from them!
I've got an MD5 Hash that looks like a Salted Hash, so we'll have to break it to see the results! By using the well known HashCat Legacy I managed to break the hash and get the password! (Using rockyou as a wordlist. Already implemented in Kali Linux and available in the net!).
It is time to use MCrypt to decrypt that weird file that I've found on the FTP before..
Using the found password stark, I managed to decrypt the file found on the FTP before..
New messages and hints and it always get me more confused, damn it!
I don't know, but what I know is that I couldn't access that page directly, so I thought I will have to play with my hosts file to point it out to this address! Let's try and see..
Browsing the web page pointed in the decrypted I get to see a login form and I used the same username and password found on the decrypted file!
Interesting thing!
Finally, the second kingdom flag is done!
I feel like we are back again to another steganography challenge on the Stark Shield Picture.
Yeah I was right about my feelings :-D
The Iron Islands Fortress is the DNS Kingdom so I think this text have some relation with this kingdom! Let's try the DNS Server and see what is going on there!
Googling and Asking some friends didn't lead to anything! Now, I am getting some feelings that I am stuck, you know guys it is pretty hard and this BOOT2ROOT CTF is damn long :[
After, some minutes later I released that I have to fix the resolv.con file! Did it and boom.
BOOOM!!! Third kingdom flag is done! Awesome, new user/pass appeared also..
A new login interface appeared using the same config (hosts & resolv.conf):
Using the user/pass found on the DNS Server I managed to get it:
After that I have seen the search bar and started playing with it I was hopping for an RCE or Command Injection but nope! But, yeah :-P I have got a good result!
That's a good thing, my result was an online file manager :-D
Weird, It won't work because of the flash or java component (I think Java :3) Okay, let's find a better browser :3 Midori Browser supports the NPAPI so let's try it out! Midori didin't work so I've found a secret trick to read the flag.txt (I won't show it :-P) It will work for you guys if you use a super outdated browser :P
Content of flag.txt was this:
user/pass: robinarryn/crOwn_fOr_a_King-_
db: mountainandthevale
8fc42c6ddf9966db3b09e84365034357
4rd flag is done * . * The game is getting funny now! Hmmmm, user/pass again!!! It was giving a hint saying the vale blabla.... Actually, the vale kingdom is the Postgresql Kingdom, so let's try that service!
After googling to how to interact with PostgreSQL I found something called psql (PostgreSQL Interactive Terminal).
Okay now, googled again and get to know how to interact with the database so I just listed the content first!
Now, I listed the Tables of that Database:
After dumping the whole content I get to know that some words are converted using the ROT16 Algorithm (It is a substitution based algorithm if I am not wrong since I don't know much about cryptography but I can crack stuff :-P) and yeah it was easy to get them back, let's get them back right now!
So it gave me 13 login IDs with the password of “ValarMorghulis”. Let's try until we get the correct one :-3 What a boring day!!!
In the first row you get another secret flag *.* Yummmi <3
I am honestly tired; I dunno how I can finish the whole number of 11 flags!! Even this walkthrough is damn long lot of explanation and pictures :'(
Okay okay, I went back and checked everything and saw Flag in my face went into that DB and I managed to read the flag through an SQL Query (SELECT * FROM flag;)..
Kingdom Flag number 5 is done! (bb3aec0fdcdbc2974890f805c585d432) and some text:
Nice! you conquered the Kingdom of the Mountain and the Vale. This is your flag: bb3aec0fdcdbc2974890f805c585d432.Next stop the Kingdom of the Reach. You can identify yourself with this user/pass combination: olennatyrell@7kingdoms.ctf/Hlgh.Gard3n.powah
but first you must be able to open the gates
Note: I am going to stop the walkthrough because I am honestly not learning anything and everything was easy/medium nothing HARD really so I am tired and I couldn't continue! Sorry, thanks for reading the walkthrough..
Here is a list of total flags I found:
2 Secret Flags:
8bf8854bebe108183caeb845c7676ae4
3f82c41a70a8b0cfec9052252d9fd721
5 Kingdom Flags:
fb8d98be1265dd88bac522e1b2182140
639bae9ac6b3e1a84cebb7b403297b79
5e93de3efa544e85dcd6311732d28f95
8fc42c6ddf9966db3b09e84365034357
bb3aec0fdcdbc2974890f805c585d432














































This short article posted only at the web site is truly good.
ReplyDeleteThanks! I appreciate your feedback.
DeleteWe would like you to definitely find out more about Farmville and it features, therefore we've created a helpful quick guide. Our objective would be to assist you to decide whether online casino osterreich Warm Qualities is really right for you! It’s all about a fun concept and also the ultimate in casino-style live roulette motion https://online-casino-osterreich.at/!
ReplyDelete